The History of Cryptography and Its Connection to Blockchain
Encrypting information to protect its confidentiality has been practiced for centuries. However, modern cryptography encrypts electronic information using complex mathematical algorithms and advanced computing, with modern blockchains and cryptocurrencies based on this technology.
The history of cryptography dates back to the Stone Age, then it was utilized in securing and protecting information. These old encryption methods have progressed into more advanced and sophisticated mechanisms. Despite its importance, many people are unaware of the history and origin of cryptography.
Let’s look at the history and origin of cryptography, its timelines, and some of the most famous algorithms that have been used over the years.
Early Days
Over 2000 years ago, Julius Caesar came up with an ingenious way to pass secret messages using an algorithm—the same method used today by banks and military forces worldwide. This way Ceasar essentially laid the groundwork for the ancient cryptography.
Julius Caesar isn't renowned as much for his contributions to the history and development of cryptography as he is to leadership and literature. Even though, his name lives on in what has become a standard technique when securing data—the Caesar cipher (or shift cipher).
Caesar cipher
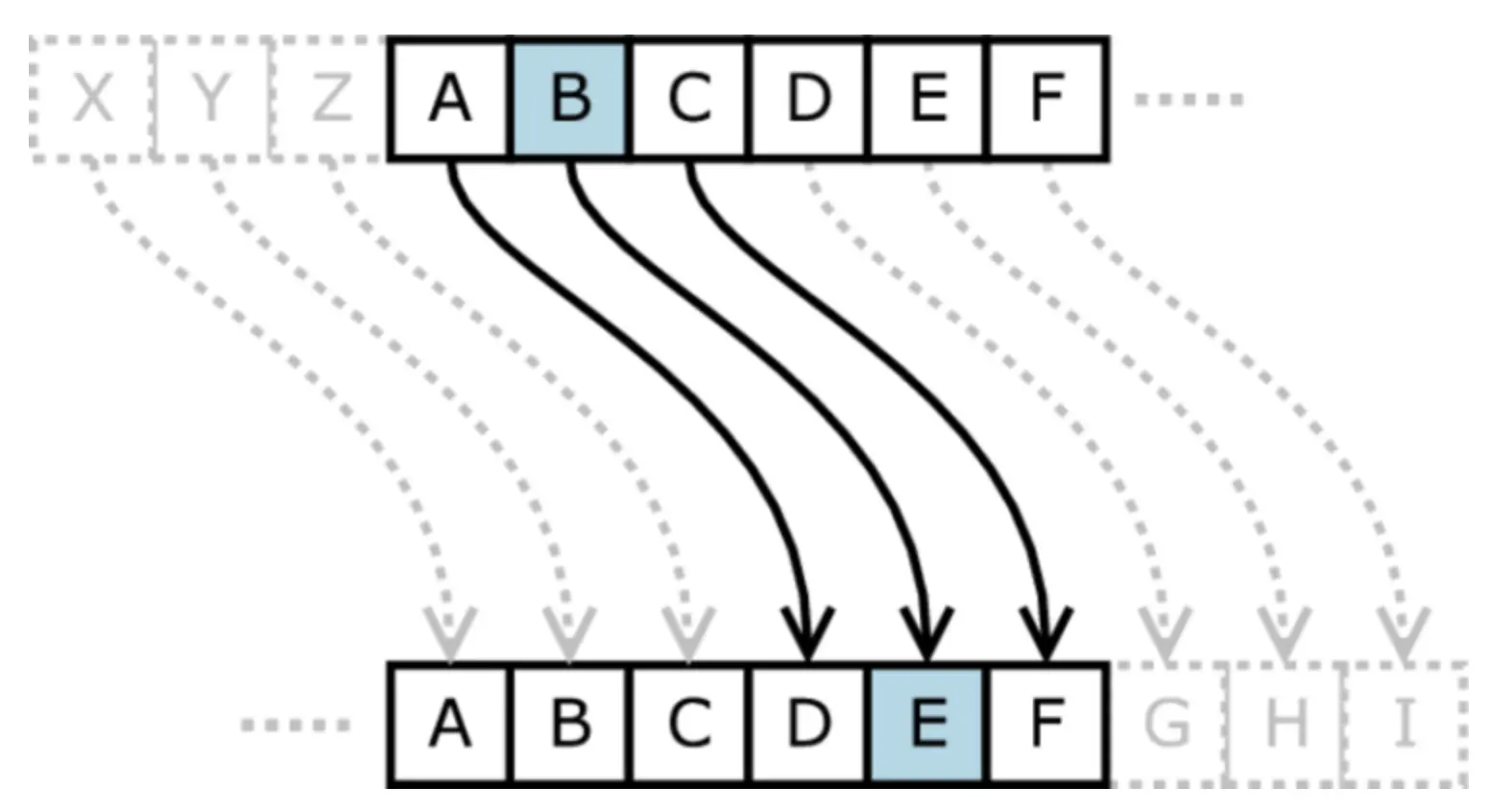
This method involves replacing letters with other letters or symbols, either by shifting every letter forward by X amount of positions (as done with Roman numerals) or by rotating each letter until it is replaced.
For thousands of years, people have used cryptography to keep their secrets safe. In ancient Egypt, hieroglyphics were used to send secret messages between spies. However, hieroglyphics is not a perfect example of cryptography techniques.
In Medieval Europe, Mary Queen of Scots was protected by ciphers when she sent messages back and forth with her supporters in England. Modern-day cryptography is no different.
Today, banks use cryptography to keep their personal information secure using encryption. This has helped us build massive networks where we can do business globally. We explore the history of the cryptography timeline relating to middle age.
Medieval and Renaissance Periods
As earlier established, the history and origin of cryptography date back many centuries—the word itself is derived from Greek words meaning hidden and writing. The art of protecting information goes back to at least 500 BC when Babylonians used cryptography to communicate secret messages.
Encoding a message was necessary for sending secret orders to military units. However, these earlier ciphers weren't truly encryption when compared with today's systems: they were based on substitution alphabets (like in Pigpen) rather than more complex modern codes that use different methods, such as transposition or polymorphism.
It wasn't until much later that more advanced codes were developed by civilizations including Ancient Greece, Rome, India, Japan, and China—ultimately laying the groundwork for what we consider modern cryptography today. So what was the earliest reason for the use of cryptography? What is the origin of cryptography? And who invented cryptography?
Well, no one knows exactly who invented cryptography or who first developed these techniques, but there are some strong candidates. Historians have made several educated guesses about prior uses of rudimentary ciphers!
What was referred to as the earliest reason for the use of cryptography was when it was employed to encode military orders. And then, many centuries later, Arab merchants are said to have employed simple substitution codes to protect trade secrets during their long caravans across Asia and North Africa.
But even if those stories aren't true, cryptography still played a major role in shaping human history. For example, cryptography enabled people to communicate and share ideas when religious differences caused societal unrest.
Leone Alberti devised a polyalphabetic cipher during middle age. A method of encoding communications that uses two separate alphabets. The first alphabet contains the original message, while the second contains a separate alphabet into which the message is translated once encoded.
Alberti cipher
The use of polyalphabetic ciphers dramatically increased the security of protecting and encoding information. However, the frequency analysis technique was of no use except if a user knew the first alphabet from which the message was encoded.
Advances in More Recent Centuries
We've seen advances in more modern forms of cryptography in more recent times, thanks to mathematical geniuses such as John Dee.
However, even though these advances are considered ancient by today's advanced cryptography approach, we haven't made nearly as much progress since then. Cryptography is most often used to secure computer data or digital signatures. It can also be used to verify transactions conducted with cryptocurrency.
Cryptography has been a long-standing mystery, but one man finally made a more significant achievement. In 1790, Thomas Jefferson invented the machine called the cipher wheel. It's a giant puzzle with rotating disks with all 26 letters on them. He wanted to keep his messages secret from anyone who tried to read them. Jefferson's method of encryption worked perfectly, and it is still in use today.
The Enigma machine, a classic example of analog cryptography, was introduced during WWII. The device was similar to the wheel cipher in that it was supposed to encrypt communications using axis powers and moving wheels, making it impossible to decode the encoded messages without another enigma. Alan Turing became famous for his work on deciphering encrypted messages using 36 enigma machines. The machine called "The Bombe" was built to try every combination possible until the encrypted message is decoded.
Cryptography in Today’s World
First, people wrote messages on paper that they then wrapped around a hard object (like a cylinder) in ancient times.
This made it harder for enemies to read their communications. The recipient could then pull out a blackened sheet of papyrus from inside the rolled-up scroll to get the secret message. Although one of the old encryption methods, it does perfectly depicts symmetric-key encryption: a single key opens or locks both sides of the communication.
Today, computers use a special set of math equations known as public-key encryption to secure everything from email to online banking. Public-key encryption involves two different keys: one public and one private. A message with a public key can only be decrypted with its corresponding private key. This is one of the prominent examples of cryptography in today’s world.
Encryption and Decryption
Encryption is a means of encoding information in such a way that only authorized parties can read it. Encryption schemes are often used to send secret messages and historically have also been used to create a secret code that can be cracked by authorized parties but reveals nothing about what has been encoded.
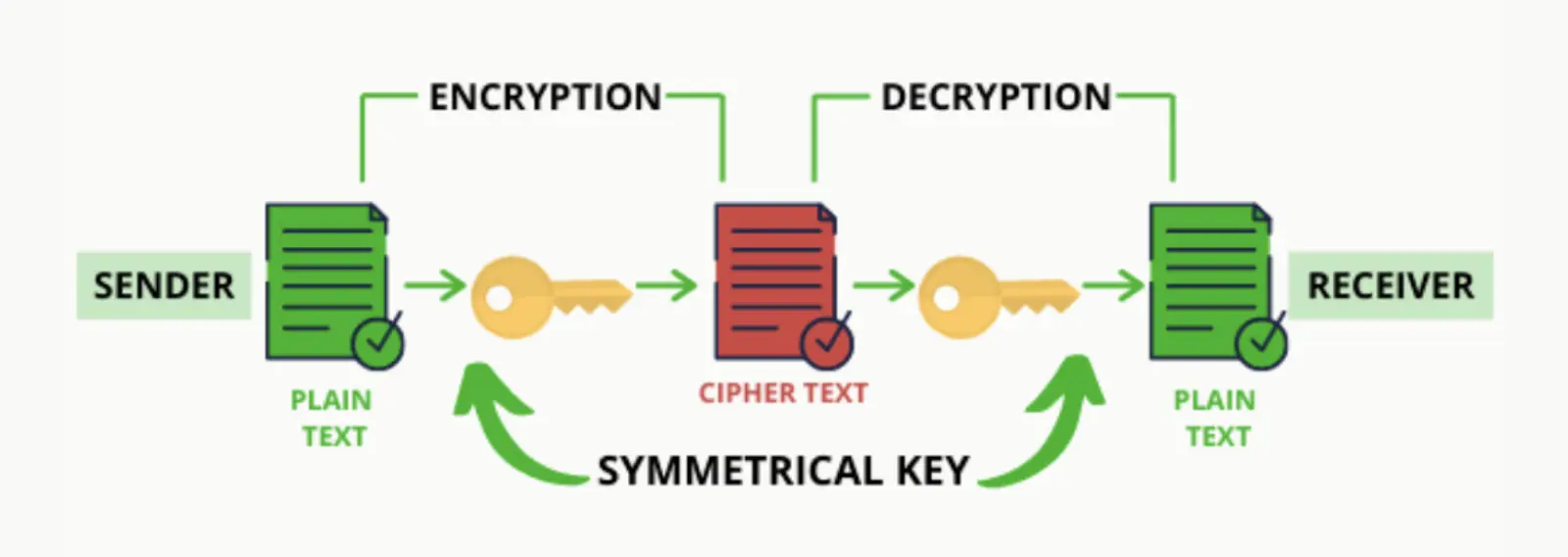
On the flip side, decryption is an analogous process for turning encrypted data back into its original form to make it readable once again. There are two main cryptographic algorithms: symmetric and public key algorithms.
In symmetric-key cryptography, a single cryptographic key is used to encrypt and decrypt data; in public-key cryptography, each party involved uses their own set of keys (private & public) to encrypt/decrypt messages exchanged between them.
Examples of encryption include old encryption methods like transposition ciphers—which were thought up thousands of years ago—and more modern techniques like RSA encryption.
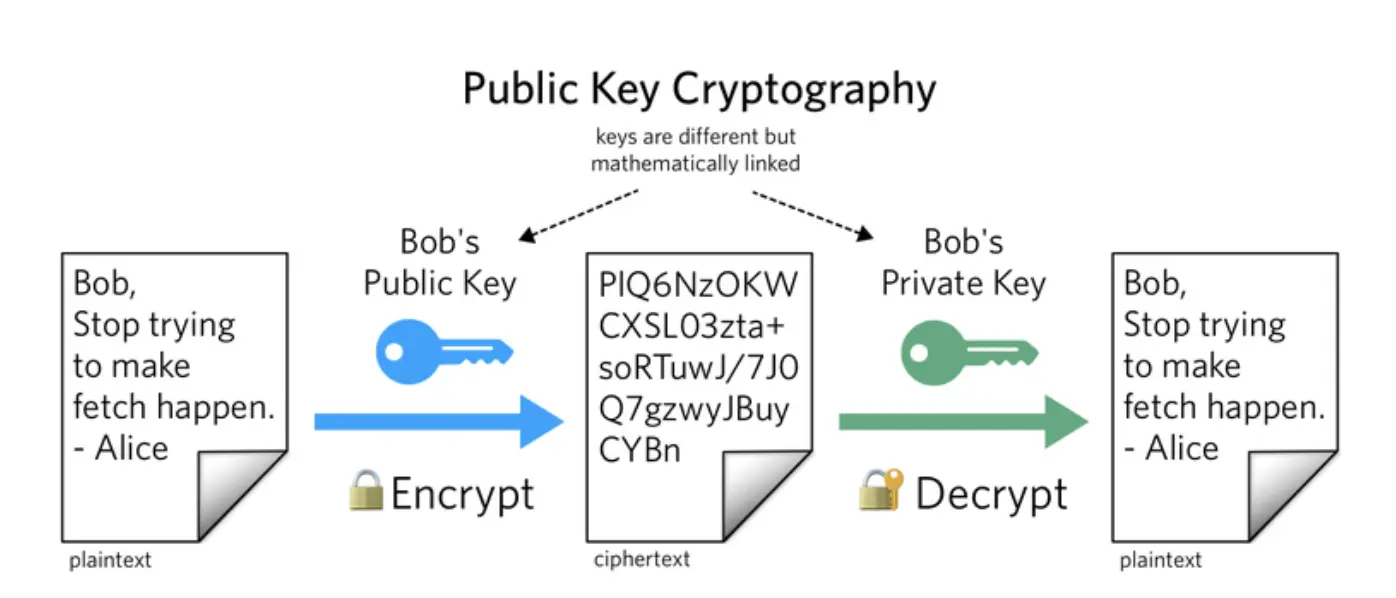
Asymmetric and Symmetric Encryption
Let's dive into asymmetric encryption. Asymmetric encryption is a type of cryptology that relies on two keys to ensure security; one encrypts messages while the other decrypts them. The first key, the public key, is used to encrypt messages while only the paired private key can unlock them. This means that anyone can use your public key to send you an encrypted message, but only you will be able to read it since your private decryption key stays hidden.
Symmetric encryption is a form of cryptography that uses one key for both decryption and encryption. However, the challenge with this method is that it requires two parties to share the same information to communicate securely using their shared secret key. It is also called private-key or single-key cryptography.
While asymmetric encryption offers more flexibility in terms of how you want to exchange data (you don't need to rely on a third-party service), it is more complex than its counterpart.
How Is Cryptography Used Today?
How is cryptography used today? Well, we had established that the history of cryptography dates back to ancient times when people first started communicating secretly. For centuries, there were few practical ways to communicate safely; if you wanted to send a spy instructions about how he should infiltrate your enemy's castle, you had to whisper them directly into his ear.
Nowadays, there are myriad opportunities for shady characters—or criminal organizations—to intercept our communications and steal our secrets. For example, email can be hacked by computer viruses or intercepted by criminals who disguise themselves as wireless internet providers.
Even something as innocuous as sending somebody an SMS text message over a cell phone leaves us vulnerable to eavesdroppers. Public-key encryption ensures that nobody besides us can decrypt our private messages; even advanced hackers would have no luck trying to crack a cryptographically secured file. There are four advantages to using a complex cryptographic system:
- Confidentiality: your private information can never be disclosed to anyone except authorized by you.
- Authentication and identification: complex cryptography allows both the sender and recipient to identify and authorize information before exchanging it.
- Non-repudiation: a user cannot disclaim the transmission and creation. The provider promotes the digital traceability and legitimacy of a transaction.
- Integrity: any form of modification of information during a transaction is detectable.
A cryptographic system combines any of the mentioned features for an intended transaction or application.
Future of Cryptography: Cryptocurrency and the Blockchain
The use of cryptography in blockchain development has greatly impacted the security and privacy of the technology and the future will likely continue the trend of symbiotic relationship. The evolution of Zero-knowledge proofs and multiparty computation is a testament to this. The former allows the prover to communicate the truth of a particular piece of information to the verifier without providing any more information, while the latter allows for secure and discreet computation on distributed data without ever exposing or moving it.
Furthermore, the crypto space has seen verifiable delay functions try to replace the energy-intensive proof-of-work consensus, and while it is still yet being improved for mainstream adoption in blockchain technology, the progress we have made so far is admirable.
Developing better cryptographic alternatives for existing blockchain algorithms is one uphill task, but the more difficult work will come in creating a compelling user-experience and updating all existing features to the new standard.
Is Blockchain Exempted?
With blockchain, asymmetric cryptography links blocks of data to generate new technology: blockchain decentralized apps, transactions, and systems. So, aside from making the internet safe and secure for everyone, it presents users with more opportunities to carry out transparent transactions.
You guessed it right; the history or origin of cryptography through each timeline is practically the history of man's relentless effort to find means aimed at securing and protecting information. Without this technology in place, the digital age would have been impossible.
*This communication is intended as strictly informational, and nothing herein constitutes an offer or a recommendation to buy, sell, or retain any specific product, security or investment, or to utilise or refrain from utilising any particular service. The use of the products and services referred to herein may be subject to certain limitations in specific jurisdictions. This communication does not constitute and shall under no circumstances be deemed to constitute investment advice. This communication is not intended to constitute a public offering of securities within the meaning of any applicable legislation.




