What Constitutes a Secure Blockchain?
The blockchain technology has gained application far beyond bitcoin thanks to its inherent security features. The decentralized nature of the blockchain, underlying cryptographic algorithms and consensus mechanism make it resistant to real attacks. As a result, many industries are exploring its potential to enhance transparency, security, and efficiency in their operations.
In this blog post, we’ll look at the blockchain, its features, and the role of cryptography in ensuring blockchain security.
Blockchain Explained
What exactly is a blockchain you may ask?
A blockchain is a shared database. This means that the entire information on the blockchain system is disseminated among a vast network of computers, which are referred to as nodes. Information is stored on a blockchain network, typically in digital format through electronic means.
These pieces of information are usually arranged in smaller, orderly formats known as blocks. And until a block is completed, it is not linked to other blocks. The cross-linking of several blocks forms a blockchain. It should be noted that any data input on the blockchain network is permanent and cannot be changed or reversed, which is often regarded as one of the main benefits of blockchain.
Each node in the network has a copy of the entire ledger, and transactions are verified by a consensus mechanism. This means that for a transaction to be added to the ledger, a majority of nodes must agree that the transaction is valid. This consensus mechanism, along with the cryptographic defense, ensures the security and integrity of the record of transactions.
The impact of blocks, and by extension, the blockchain technology in the crypto ecosystem, cannot be overemphasized. Apart from being vital in running numerous cryptos, including Bitcoin, its continuity method also ensures that details of digital transactions can be trusted.
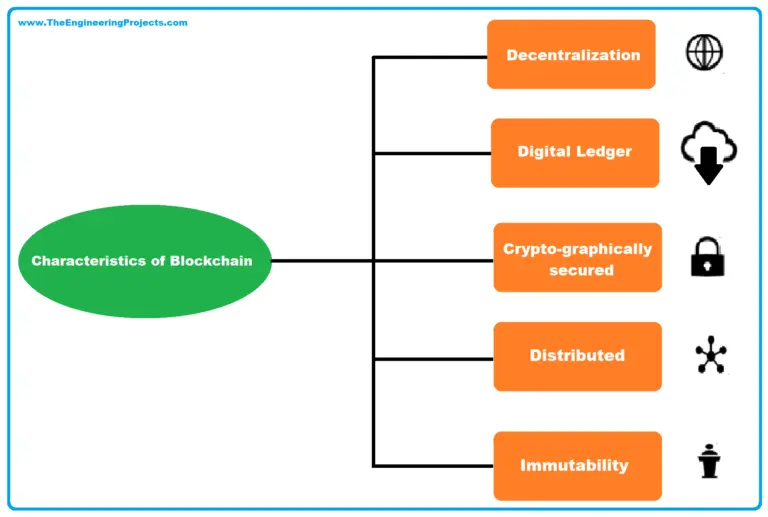
Features of Blockchain
A blockchain system has five crucial defining features. They are;
1. Network Distribution
A blockchain runs using a disseminated or distributed network. This means that the responsibilities of validating blockchain transactions are not concentrated in the hands of a central authority.
Rather, the processing of transactions is disseminated evenly among several people, known as nodes. Individual nodes can validate or confirm transaction blocks with no external influence.
This feature helps secure the blockchain as any malicious trade, purchase, or transaction will be easily detected and stopped because of the shared network.
Additionally, this distributed nature reduces the risk of routing attacks, where a malicious actor intercepts and alters communication between nodes because the information is not transmitted through a single route but is distributed across multiple paths.
2. Immutability
The idea behind this is simple—blockchain transactions are permanent and cannot be altered after validation. Each transaction carried out is accurately captured, alongside the time, date, and any additional data connected to the person carrying out the transaction. This permanence ensures the integrity of the record of transactions and reduces the risk of fraud and other security vulnerabilities because once the data is recorded, it cannot be altered by any party.
3. Consensus Mechanism
For any decision to be made on the blockchain network, there must be a unanimous agreement between all functional parties (nodes) using a consensus model. This ensures that the decisions made are in the best interest of most of the network users.
Moreover, the consensus mechanism plays a crucial role in preventing double-spending, a common type of attacks in digital currency systems where a bad actor tries to spend the same digital currency more than once.
4. Unique User Signature
Even though the blockchain system is ‘faceless,’ there is a means of identification peculiar to every user — private keys. A blockchain participant has private keys whose codes are known only to them. These keys prevent fraud or impersonation if kept properly, thereby contributing to a secure blockchain.
5. Cryptographic Defense
As previously indicated, changing blocks that have already been recorded on the blockchain network is almost impossible. Cryptography's immutability and dependability combine to make block generation and linking a safe operation. If someone tries to modify the contents of a block, the chain will break, alerting all network nodes immediately. No matter how hard someone tries, the blockchain persistently rejects all hacking attempts.
Cryptography: Its Significance in Sustaining a Secure Blockchain
The history of cryptography can be traced back to ancient times when people first began communicating secretly. Cryptography is an indispensable component of any blockchain network ensuring that a secure blockchain is maintained at every point. The Bitcoin blockchain has gained a reputation and is well known over time to be impossible to hack.
However, cryptography is a crucial backbone behind the high immunity of the Bitcoin blockchain. It ensures that digital money in a user's crypto wallet remains safe and untouched.
How Cryptography Works
Cryptography is a fundamental component of blockchain technology, playing a crucial role in both public blockchain and private blockchain networks. It mainly functions through a process known as hashing. During this process, data of any size is usually entered into an algorithm, and in return, it yields a hash of a predetermined length or size. The algorithm is referred to as a hash function. This hash function ensures that the data in each block is securely encrypted.
Every hash is made up of data, and any alteration to the data found within the block will lead to a corresponding alteration of the main block hash. This characteristic is essential for maintaining the privacy and integrity of the data stored on the blockchain. It is also a key feature that differentiates blockchain from other types of databases. In traditional databases, data can be altered or deleted, but on the blockchain, once the data is recorded, it is permanent and immutable.
Every hash comprises two main things; the data contained within the block itself and the data in the block before it. These hash markers are significant players vital to sustaining and securing the blockchain, whether it is a public blockchain, private blockchain. This is because the hash markers create a chain of dependency among the blocks. Each block is dependent on the one before it, creating a chain of blocks that is extremely difficult to alter once recorded.
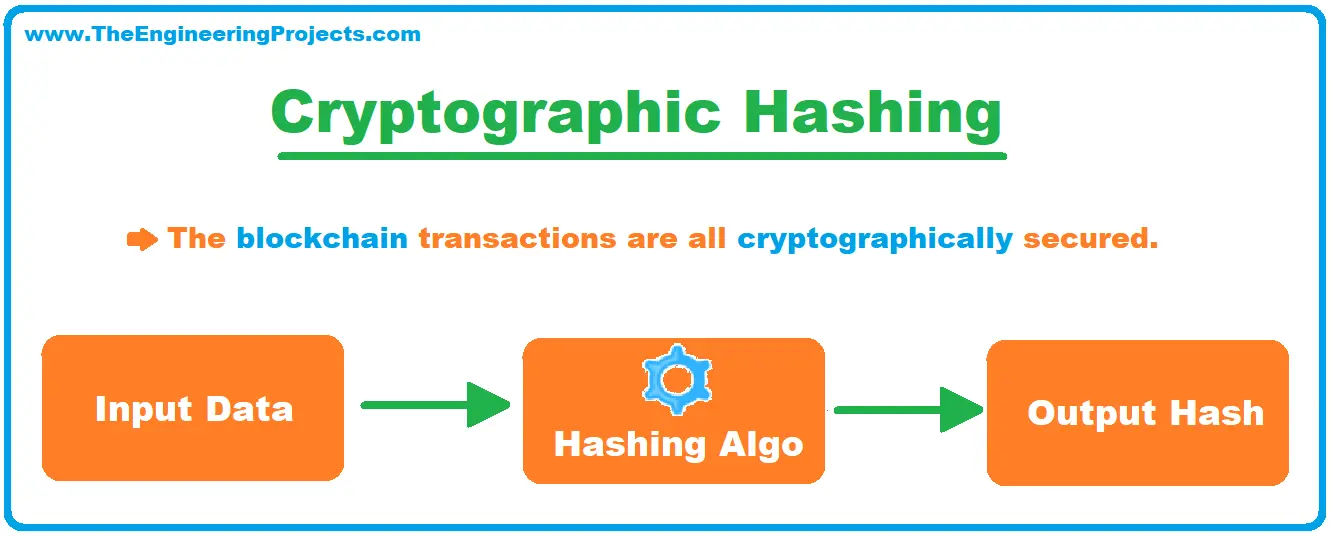
Every new hash is generated on the backbone of the one before it, which leads to a cross-link between data blocks. This cross-linking is what creates the 'chain' in blockchain. It ensures that all the blocks are connected in a specific order, creating a permanent and tamper-proof record of transactions.
The Bitcoin blockchain, for example, uses the proof-of-work (PoW) agreement model. This PoW model functions using an algorithm known as SHA-256. What the code simply implies is that as soon as data is passed into the algorithm, it produces a 256-bit hash that is made up of 64 characters. This hash, made up of 64 characters, is unique to the data inputted into the algorithm. Even a small change in the data will result in a completely different hash.
This cryptographic process is fundamental to the operation of blockchains, ensuring data privacy and security across the network.
Additional Functions of Cryptography
As earlier established, much of Blockchain's success can be owed to cryptography. For instance, mining power is crucial for the operation of Bitcoin and Ethereum, and the security of the mining pools is heavily reliant on cryptography.
A crypto wallet is a must-have for anyone intending to participate actively in the cryptocurrency market, be it via investing or Bitcoin mining. These cryptocurrency wallets function as a store for a user’s funds and investments, similar to commercial banks. However, unlike commercial banks, which use centralized ledger technology, cryptocurrency wallets are based on decentralized ledger technology, which provides additional security.
A form of cryptography, referred to as asymmetric cryptography, is responsible for the generation of both private and public keys that facilitate the receipt and sending out of payments. This is a fundamental aspect of the security infrastructure of major cryptocurrencies, Bitcoin and Ethereum. The private keys are additionally utilized to create unique signatures for each user. These keys serve as a form of identification and confirmation to ascertain the person carrying out the trade.
The cryptographic nature of these keys ensures that only the holder of the key has access to his crypto wallet, making sure the funds are kept safe. This is a critical feature that protects users' funds from various types of attacks that have been observed in the cryptocurrency space. The importance of cryptography in securing the blockchain cannot be overemphasized. It is the backbone that ensures the security and integrity of all transactions on the Bitcoin and Ethereum networks.
Other Factors that Secure the Blockchain
Crypto economics, a rather novel concept, can also maintain blockchain security. This concept is a product of game theory, a model used to make decisions with a collection of predetermined rules and rewards, and is mainly mathematical.
Unlike the conventional game theory, which has a wide range of descriptions, the conduct of nodes across a disseminated computer network is distinctively described as crypto economics. This distinction arises because the behavior of nodes in a blockchain network is influenced by economic incentives and cryptographic verification.
Crypto economics may also refer to the study of the economics behind the protocols of a blockchain network and the conduct of individual players, including the outcome of their collective input. It encompasses the study of incentives that drive the behavior of network participants and the security properties of the network.
The model provides blockchain security through the assumption that since the smooth running of the network is more beneficial for nodes, it will be more helpful for them to be on their best behavior rather than sabotage the network. A good example of this concept is seen in Bitcoin mining, where miners are incentivized to validate transactions and add them to the blocks because they are rewarded with newly minted bitcoins and transaction fees.
By initial design, Bitcoin mining is an expensive process that needs vast amounts of resources and computing power. As a result, it consumes a lot of time, energy, and money, irrespective of where, how, and when the mining is done.
Because of the complexities involved in the network, antagonistic conduct is severely frowned upon, while desired behavior is compensated. This compensation creates a system where it is more profitable for nodes to act honestly and contribute to the network's security.
As soon as a particular node is noticed to be malicious or shady, such a node will be kicked off the blockchain. Good and competent system nodes also have a high probability of receiving significant rewards for their honest conduct, creating a strong disincentive for nodes to act maliciously, as they would lose their rewards and be excluded from the network.
This risk-reward equilibrium of nodes will guard against invasions of the network, such as 51% attack. The 51% attack, mostly considered a blockchain limitation, will only work out if a hacker gains 51% control of the entire network. But, because of the huge volume of participants on the Bitcoin network platform, the likelihood that an attacker will successfully compromise the network is slight, if not impossible. Additionally, the cost of acquiring the computing power necessary to launch a 51% attack would be prohibitively expensive.
Aside from that, the computing power required to compromise 51% of the network would be huge. Therefore, taking over the network would not be economically rational, as the cost of it would far exceed any potential gains.
It would be a bad idea to spend so much money to gain only a fraction of the money spent to compromise the network. The ability of an online blockchain system to still work despite one or a few nodes becoming selfish is the consensus model used in Byzantine Fault Tolerance (BFT) protocols. These protocols are designed to ensure that a distributed network can reach consensus and continue to function even if some nodes fail or act maliciously.
So far as the demerits of sabotaging the network are more than the potential benefits, and as long as the good nodes are continuously recognized and compensated, the blockchain network will last a very long time, devoid of major hitches. Ultimately, the economic incentives and cryptographic verification mechanisms built into the network ensure that it is in the best interest of all participants to act honestly and contribute to the network's security.
Concluding Thoughts
With the advent of cryptocurrency, especially Bitcoin and Ether, blockchain has massively grown in popularity and use. So far, the technology has provided top-notch security and decentralization to its users across various networks using a combination of cryptography, crypto economics, and additional mechanisms. However, as the technology matures, it's important to continually address vulnerabilities that could potentially compromise these networks.
Many crypto projects are being run on blockchain technology, leading to millions of cryptocurrency wallets being supported on the blockchain. This widespread adoption underscores the critical role that this technology plays in the modern financial ecosystem. The large number of users and the necessity to protect each user’s digital money make securing a blockchain of utmost priority. In particular, the rise of private blockchain network and permissioned blockchains has added another layer of complexity to the security landscape, making the task of addressing vulnerabilities even more critical.
*This communication is intended as strictly informational, and nothing herein constitutes an offer or a recommendation to buy, sell, or retain any specific product, security or investment, or to utilise or refrain from utilising any particular service. The use of the products and services referred to herein may be subject to certain limitations in specific jurisdictions. This communication does not constitute and shall under no circumstances be deemed to constitute investment advice. This communication is not intended to constitute a public offering of securities within the meaning of any applicable legislation.




